Given the many instances of email security compromises, it has become vital to provide additional security to emails from the domain administrator level. Security protocols such as Domain-Based Message Authentication, Reporting and Conformance (DMARC), Domain Keys Identified Mail (DKIM), Sender Policy Framework (SPF) and Brand Indicators for Message Identification (BIMI) to prevent address spoofing are considered below.
Before getting into the security protocols, spoofing needs to be understood. Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source. Spoofing can apply to emails, phone calls, websites, IP address, etc. In email spoofing, an email header is forged so that the message appears to have originated from someone or somewhere other than the actual source. The objective is to get recipients to open/respond to the emails. There are many email spoofing portals from which emails can be sent to the recipient as if they originated from the real domain; such spoofing is called direct domain spoofing. DMARC, DKIM, SPF and BIMI can be used as an authentication and validation tool in many of these instances.
DMARC is an email authentication policy and reporting protocol. It determines whether the sender uses DKIM/SPF, handles recipients for authentication failure as per policies, and improves and monitors domain security from fraudulent email. It detects such emails and discards or blocks, depending on the configuration upon receiving. DMARC addresses owners and receivers in the following ways:
Domain owners:
- Informs usage of email authentication DKIM, SPF
- Collects feedback about email messages using their domain – authentic or not
- Sets policy to report, quarantine or reject the message
Email receivers:
- Ensures the email domain uses email authentication
- Continuously evaluates SPF and DKIM along with what recipients see in their inboxes
- Ascertains domain owners’ preference of report, quarantine or reject the messages that do not pass authentication checks
- Provides email owner feedback about messages using their domain
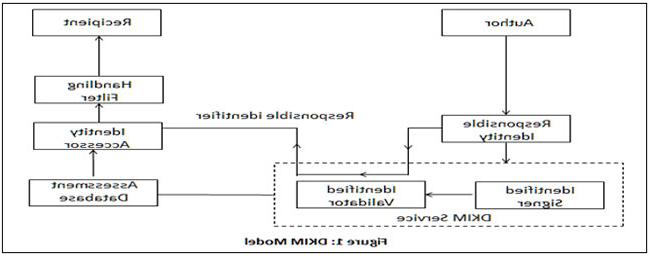
DKIM validates the identity of the email domain through cryptographic authentication by attaching a new domain identifier. It differentiates domains used by the known organization and domains used by others through Signing Domain Identifier (SDID). Figure 1 shows the DKIM model in which the process of the message validation is depicted. DKIM service provides a responsible identifier to the assessor, which assesses the identifier and assessment database and provides input to handling the filter. This filter uses various factors such as ancillary information from DKIM validation to provide input to the recipient.
SPF is a type of Domain Name Service (DNS) TXT record that identifies which servers are permitted to send email on behalf of your domain. The purpose of SPF record is to detect and prevent spammers from sending messages on behalf of your domain.
BIMI is a centralized method across multiple email providers to display the brand’s logo along with email messages. It helps to identify legitimate senders and reduce the number of fraudulent messages being opened or read. This protocol has been adopted by more than 81 leading email sending domains.
These protocols will be effective only when the email domain administrator enables in DNS using TXT records or enables an email host provider’s admin console. This is done to verify whether a particular email came from the specific domain from which it claims to be sent.
The above options are not perfect solutions for email security due to the fact that compromised email can be sent within the domain, a domain that uses DKIM and SPF can be set, and many commercial email hosts may not consider the senders’ domain settings. These protocols may provide enhanced security but are not 100 percent fool-proof. There are also cloud solutions in the market for preventing email security compromises that provide promising results.
